Chainlink CCIP - Cross-Chain Interoperability Protocol
Build with CCIP
CCIP makes it simple to move data, messages, and tokens across blockchains. Connect smart contracts on different networks as if they were one system, whether transferring stablecoins, powering cross-chain apps, or running multi-chain DeFi.

Deploy/enable a token across multiple chains
Create a new Cross-Chain-Token or enable an established one that can be launched on 50+ chains, providing unparalleled interoperability and reach.
Bridge a token
Securely transfer tokens - including ETH, USDC, LINK - and messages between different blockchain networks.
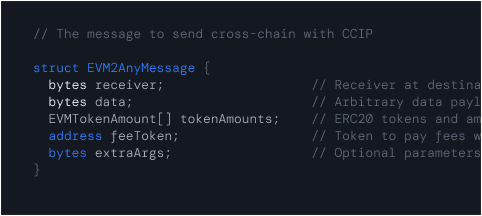
Send a token with data
Build token transfers that do more than move value, letting you embed business logic directly into your cross-chain workflows.
Tutorials
Acquire Test Tokens
Get test tokens in minutes; build and test cross-chain apps with zero friction.
Transfer Tokens
Unlock seamless token transfers from contracts; learn, code, and deploy.
Transfer Tokens with Data
Go beyond basic transfers with logic-infused token movements in your EVM contracts.
Using the Token Manager
Effortlessly manage CCTs by tracking, importing and organizing tokens from your dashboard.
Using the JS SDK
Integrate CCIP in your frontend or backend effortlessly with JavaScript SDK.
Check Message Status
Retrieve real-time status of your offchain transaction from EVM.
Transfer Tokens Between EOAs
Send tokens offchain from an Externally Owned Account with clear steps.
Using the CLI
Use offchain tools from CCIP to simplify your Ethereum workflows.
Deploy and Register a CCT
Use RemixIDE to launch and configure tokens for cross-chain transfers on CCIP.
Register CCT Burn & Mint EOA
Implement burn-mint cross-chain token logic with CCIP using Hardhat or Foundry.
Register CCT Lock & Mint EOA
Implement a lock-mint token registration workflow with CCIP and Hardhat or Foundry.
Set Token Pool Rate Limits
Update rate limiter settings for your cross-chain tokens using Hardhat or Foundry.
Quick Links
Tools & Utilities

CCIP API
An API for message retrieval and lane latency information.

Javascript SDK
Integrate CCIP functionality directly into your web applications for EVM-compatible chains.

CLI
TypeScript command-line interface and library designed for interacting with deployed CCIP contracts.

Hardhat Starter Kit
Ready-to-go boilerplate for basic CCIP use cases that help you get started building quickly with Hardhat.

Foundry Starter Kit
Ready-to-go boilerplate for basic CCIP use cases that help you get started building quickly with Foundry.

CCIP Contracts NPM
An npm package providing Solidity smart contract implementations to integrate CCIP into your EVM-based project.

Direct Staking
Stake native tokens on supported L2 networks and receive liquid staked tokens directly on the same chain.
Resources
Token Pool Types
Explore the various token pool types supported by the Cross-Chain Token (CCT) standard with Chainlink Labs. Explore the various token pool types supported by the Cross-Chain Token (CCT) standard with Chainlink Labs...
Token Pool Types
Explore the various token pool types supported by the Cross-Chain Token (CCT) standard with Chainlink Labs. Explore the various token pool types supported by the Cross-Chain Token (CCT) standard with Chainlink Labs...
Token Pool Types
Explore the various token pool types supported by the Cross-Chain Token (CCT) standard with Chainlink Labs. Explore the various token pool types supported by the Cross-Chain Token (CCT) standard with Chainlink Labs...
Given the inherent risks of cross-chain interoperability, CCIP features defense-in-depth security and is powered by Chainlink's industry-standard oracle networks which have a proven track record of securing tens of billions of dollars and enabling over $14 trillion in onchain transaction value.
CCIP's robust security framework is built upon several core components:
- Proven Decentralized Architecture: CCIP leverages the same highly reliable infrastructure as Chainlink Data Feeds, which has enabled trillions in transaction value across hundreds of DeFi applications. Cross-chain transactions are validated by multiple decentralized oracle networks (DONs).
- Rate Limiting: To mitigate risk, CCIP includes a rate limiting feature. This allows owners to establish and configure policies for Cross-Chain Tokens, which are then enforced on both the source and destination chains.
- Timelocked Upgrades: All on-chain, security-critical configuration changes and core infrastructure upgrades must pass through a Role-based Access Control Timelock contract. This process provides a review period during which CCIP node operators can veto the upgrade, or, in time-sensitive situations, explicitly approve it.
- High-Quality, Sybil-Resistant Node Operators: The system is secured by the same globally distributed, security-reviewed, public node operators that secure other Chainlink services, validate leading blockchain networks, and operate traditional Web2 infrastructure. Each independent CCIP node is run by a distinct organization with extensive DevOps expertise and rigorous private key management security practices.
To understand how Chainlink CCIP works, refer to the architecture section. If you are new to using Chainlink CCIP, read these guides before you deploy any contracts that use CCIP.